Privacy and Security Settings
Application server
The operation team accesses the application server. This is only possible by filling out a JIT-Access request. The request can only be generated by an authorized user from our organization with the required rights. To generate a request, the user has to log into his Microsoft account, which 2FA secures, access the JIT board, and fill out the form. He can allow traffic from a specific IP over a specific port for a specific amount of time (up to 9 hours).
Access to the actual server is realized by local users with a predefined password.
Database authentication (Azure SQL)
Azure AD users authenticate between the application server and Azure SQL. No passwords are stored in plain text on the application server, and a separate user is used for each Celonis Process Management instance.
Encryption of the hard disks
The hard disks are encrypted with BitLocker (AES 128 it). https://azure.microsoft.com/documentation/articles/storage-service-encryption/
Azure portal (incl. Azure Services)
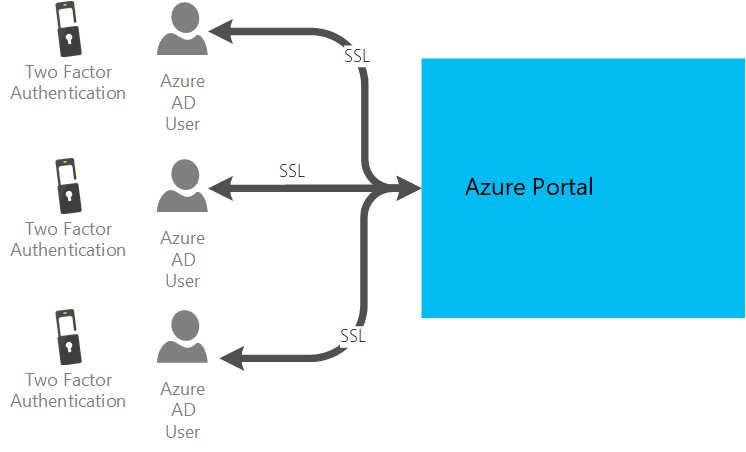
The Azure Portal is accessed by the Operations Team. Accesses are personalized via Azure AD. The corresponding Azure AD users are secured with multi-factor authentication. On trusted devices, multi-factor authentication must be renewed after 30 days.
The passwords of Azure AD users are renewed after 180 days.
Celonis Process Management access
All Celonis Process Management users are authenticated via single sign-on via SAML.
In the same way, Celonis Process Management Consultants can access the data after consulting with the customer.
This ensures that all connections between client and server are SSL encrypted.
For more details, please see the online documentation.
Inter-Service (Interop) Security
Services in the Celonis Process Management ecosystem are orchestrated by the Celonis Process Management Operations Service (Ops Service), which knows about them and the context in which they may be used:
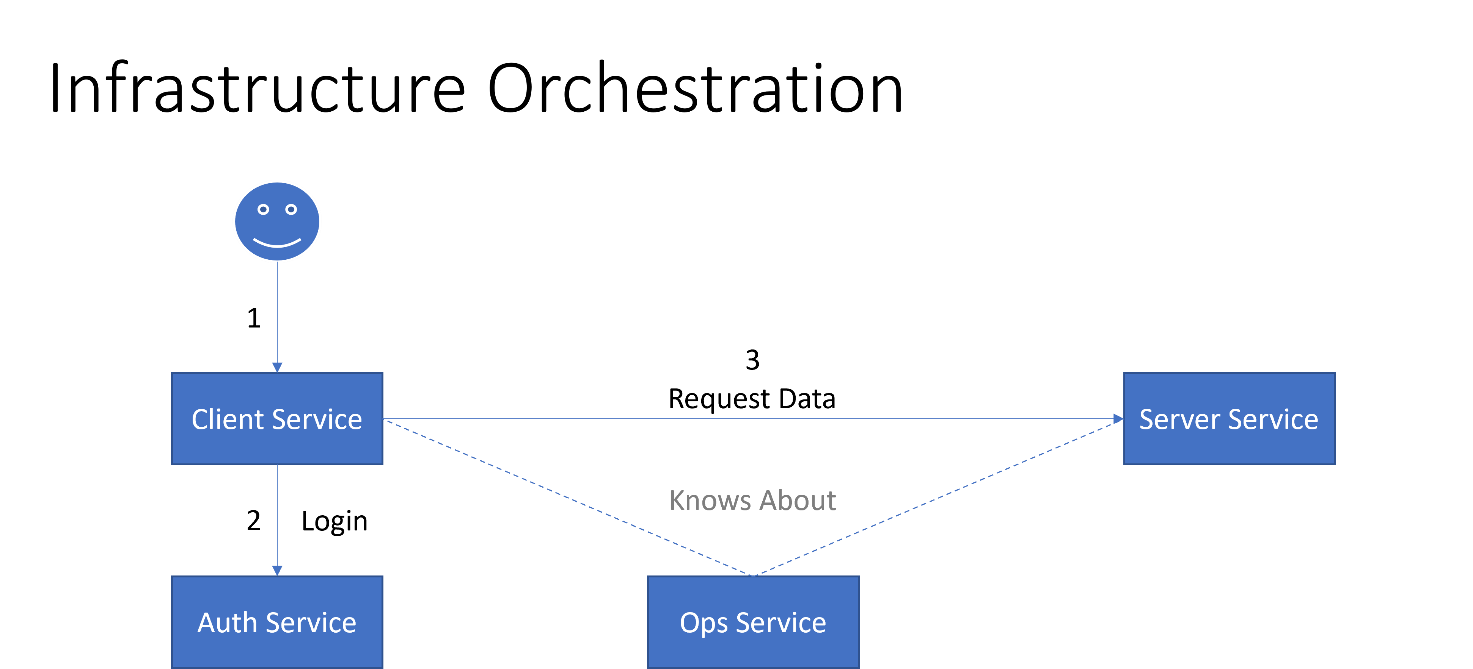
While the user login to an application is facilitated by the Celonis Process Management Authorization Service (Auth Service), the communication among services is secured by the Ops Service. This is especially true for services providing access to confidential data (in contrast of processing only provided data):
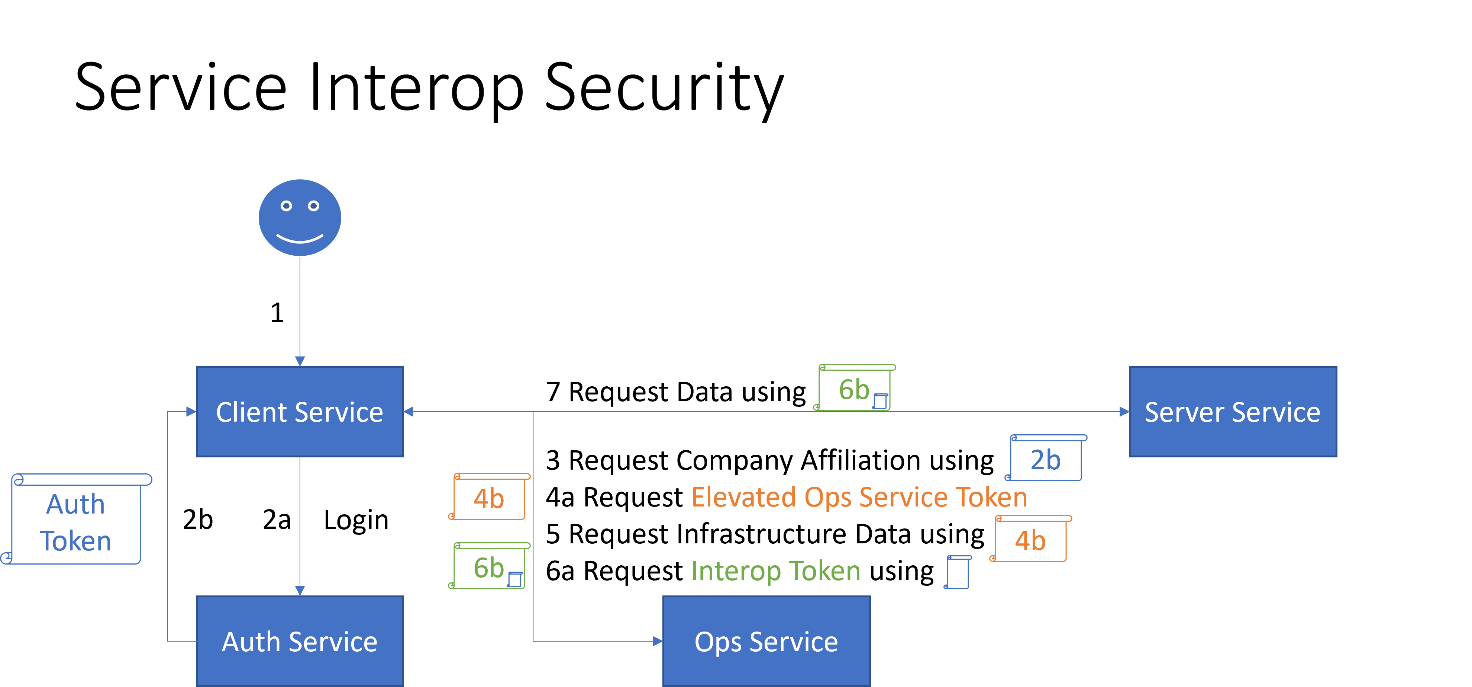
Three kinds of tokens are involved in securing application/service access:
Auth Tokens identify a user and are handed out during user login.
Elevated Ops Service Tokens identify a service and can be requested by the service to request/manipulate infrastructure data in the Ops Service that a typical user cannot normally access.
Interop identifies a user in the context of inter-service communication and can be requested by a client service for a specific user and target/server service; this token is only issued when the target service may be accessed, and the target service will be able to identify the associated user and apply for any service-specific permissions.
These tokens are JSON Web Tokens (https://jwt.io/) issued based on OpenID Connect and OAuth2 principles.