Configuring OIDC single sign-on
Your users can access your Celonis Platform using an OpenID Connect SSO, assigning each user with an ID token on login.
Prerequisites for OIDC single sign-on
To configure your OIDC SSO, you need the following from your identity provider:
ClientID
Client secret
Provider Discovery URL
You also need the following authorized redirect URL:
https://[customerdomain].[realm].celonis.cloud/api/auth-handler/oidc/callback
Procedure
To configure your OIDC SSO:
Click Admin & Settings - Single Sign-On.
Click OIDC - Configure.
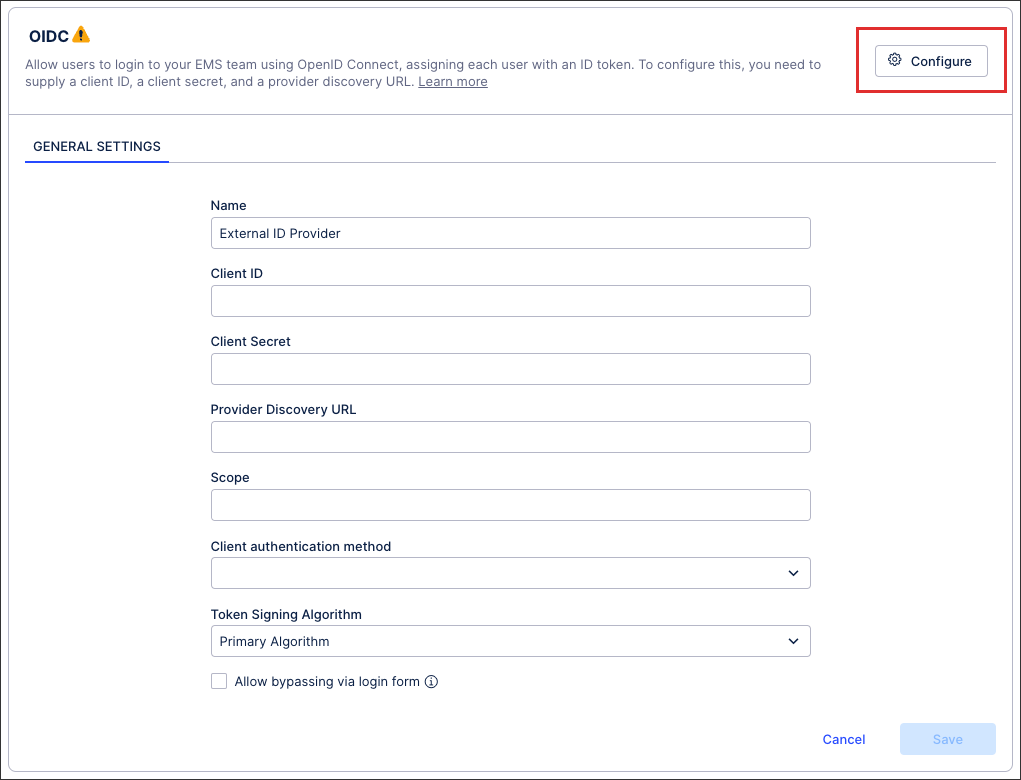
Enter the required information, including ClientID, Client Secret, Provider Discovery URL, and Scope value.
When inputting your scope value, we recommend using openID email and openid email profile .
Optional: You can also allow bypassing via login form.
Click Save.
When prompted, either click Activate or choose to activate your configuration later.
If activating your OIDC configuration later, return to the Single Sign-On screen and click Activate:
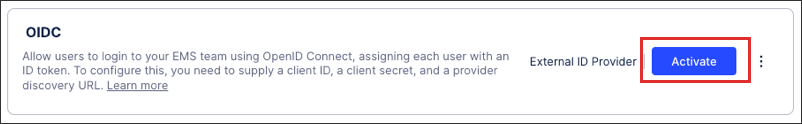
Your OIDC SSO is now active, with all active users at that point being automatically logged out of your and need to re-authenticate to regain access.
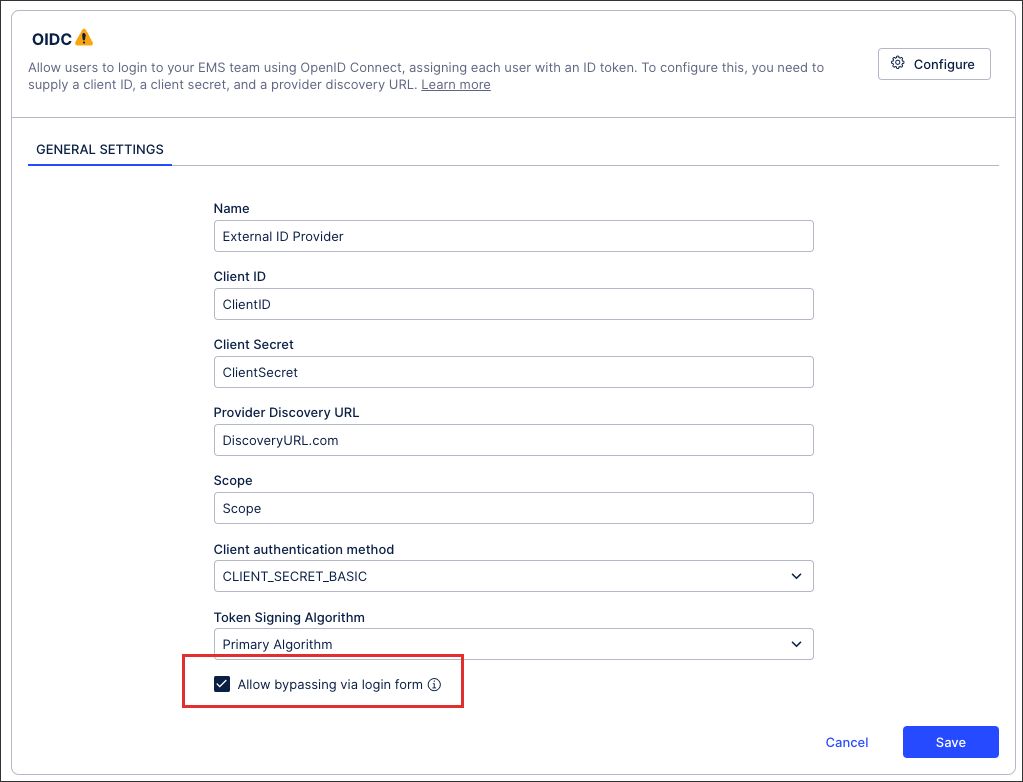
Allow bypassing via login form
Enabling this option allows users who are outside of your IdP to still access your team with their email address and password. This feature is beneficial when working on implementation projects or when adding the user to your IdP is time consuming.
 |