Configure SAML
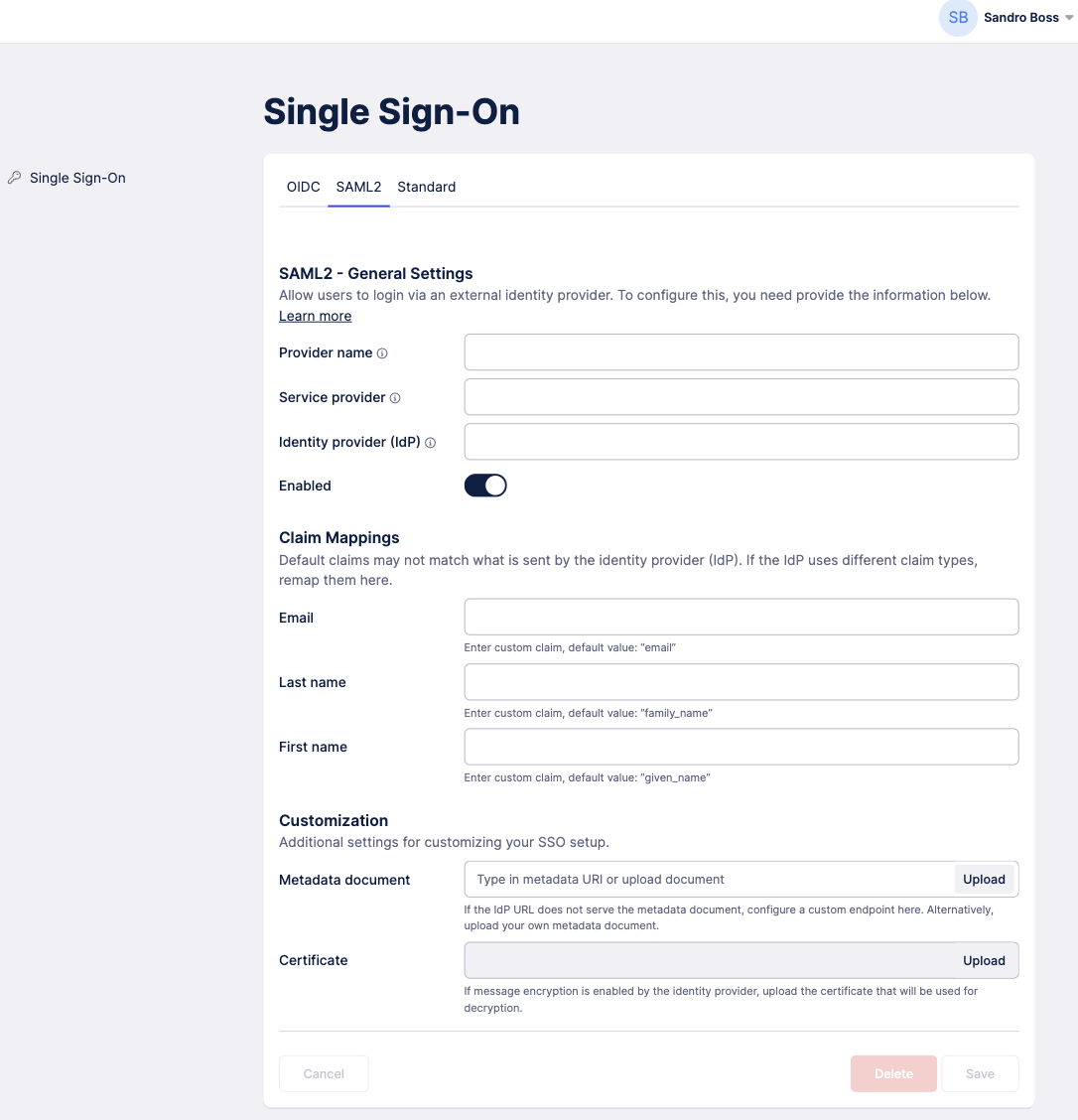
If you have a metadata file, you can upload the file under Customization and skip the configuration setup.
If you don't have a metadata file, start by having Celonis Process Management (CPM) open in one tab, and your identity provider open in another. This way, you can copy and paste information between the two as needed. If you have additional documents for SSO configuration, such as a custom certificate, you should keep them handy.
In your CPM tab, upload your metadata file or custom certificate to auto-populate the fields, if using. If not, use configuration table below to fill out each field.
Next, in your identity provider tab, check to see if your claims have custom names. If so, use the claim mappings section to map them for use in CPM.
In your CPM tab, once you've finished filling out the configuration form, click Save.
The last step is to add some additional information within your identity provider so that it recognizes the connection you just configured in CPM. Use the information in the redirect section below, and make sure to replace
companyShortNamein the sample URLs with your company's name.
Field | Description |
|---|---|
Provider name | The login provider name. |
Service provider | This is prefilled as “https://auth.symbio.cloud”, and can be any value that starts with ‘https://’ (for example: https://customer.cpm.com). This is often requested as “Entity ID” on the IdP side. Both the Service Provider value configured in CPM and the “Entity ID” that is associated with the identity provider you indicate in the IdP need to match. |
Identity Provider | Indicated on your identity provider side, usually with a URL in this format: |
Enable/Disable toggle | Enables or disables the login provider. If disabled, the button will not be shown on the login page. |
Metadata document (if applicable) | If the IdP URL does not serve the metadata document, configure a custom endpoint here. Alternatively, upload your own metadata document. Caution If a metadata document is not served/uploaded and a custom endpoint is not configured, all login attempts will fail. |
Certificate (if applicable) | If message encryption is enabled by the identity provider, the certificate will be used for decryption. |
Claim mappings: | The expected claims sent by the identity provider are
If the IdP uses different claim types, remap them here. |
Redirect URLs
Once you've finished configuring your SAML set up, the last step is to add the ACS consumer URLs to your identity provider. The companyShortName is a unique identifier for your tenant inside our systems. It can be found in the URLs provided to you for Process Designer or Process Navigator.
For example, the URLs for a company called Celonis would be:
in Process Designer:
https://symbioweb.com/celonis/demoStoragein Process Navigator:
https://navigator.symbio.cloud/celonis
You can find out what region you're in by checking the URL of your workspace in either Process Designer or Process Navigator.
Region | URLs |
|---|---|
Europe | SAML2 ACS Consumer URL: |
US | SAML2 ACS Consumer URL: |
Japan | SAML2 ACS Consumer URL: |
Customization
To configure a SAML2 identity provider, a custom metadata document can either be referenced via URI or by uploading the document. Likewise a custom certificate file can be uploaded. For more information on certificates, refer to Certificate management for SAML single sign-on.