SAP SSO for personal dynamic connections
This feature is currently available as a Private Preview only
During a Private Preview, only customers who have agreed to our Private Preview usage agreements can access this feature. Additionally, the features documented here are subject to change and / or cancellation, so they may not be available to all users in future.
For more information about our Private Preview releases, including the level of Support offered with them, see: Feature release types.
Authenticate with SAP using Single Sign-On (SSO) when triggering an action in SAP directly from Celonis. By executing actions under the user’s personal connection, it ensures better traceability and auditability, while also enhancing security by eliminating the need for shared credentials.
Note
SSO applies to attended automation use-cases, for instance when a user clicks on an Action button or a Task in a View, which triggers an Action Flow to update SAP and the update is performed with the user’s personal SAP account. For unattended automation use cases, we recommend using a generic/service SAP account for these cases.
Java version 21 or later
On-prem Client (OPC) version 1.3.1 or higher (see Installing on-prem clients)
Note
If you run a (legacy) Automation Agent, you must migrate your setup to OPC first.
Your Celonis Platform is connected with SAP using SAP Java Connector. See Connecting to SAP.
Secure Network Communications (SNC) is established between OPC and the SAP server. See the setup steps here
You have Admin access to (pre-)production SAP
You have Admin access to Celonis Platform
Relevant BAPI permissions are assigned to the business users who are going to perform actions in SAP from Celonis. Note that BAPI permissions are different from TCode GUI permissions.
Before you start, please ensure login/certificate_mapping_rulebased profile parameter is enabled. Once Secure Network Communications (SNC) is configured, follow the steps below to enable the SSO integration:
Ensure “Entry for certificate” option.
Log in into SAP GUI and open t-code SM30.
Open table VSNCSYSACL.
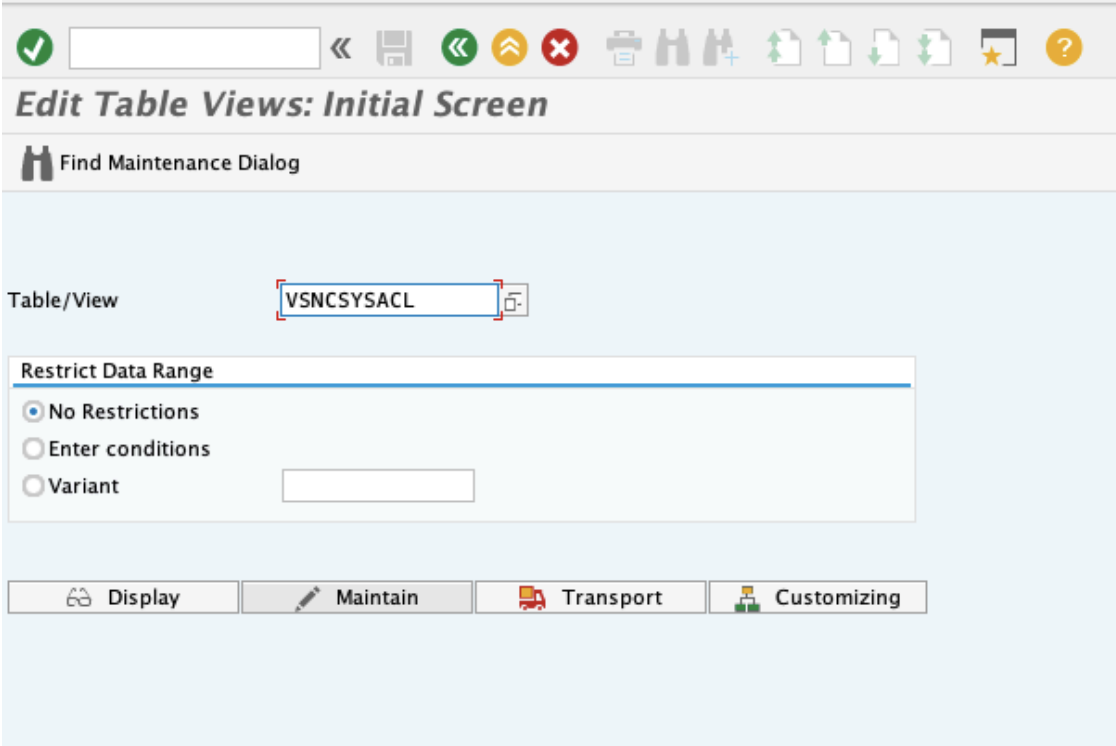
Press E for External.
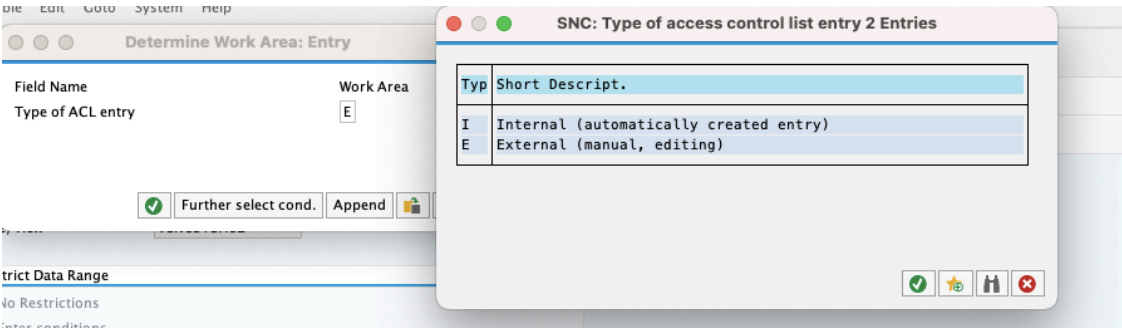
Select the system ID entry for Celonis OPC.
Click New Entries.
Enter the name of the OPC Automation Agent SNC.
Click entry for certificate activated.
Click Save.
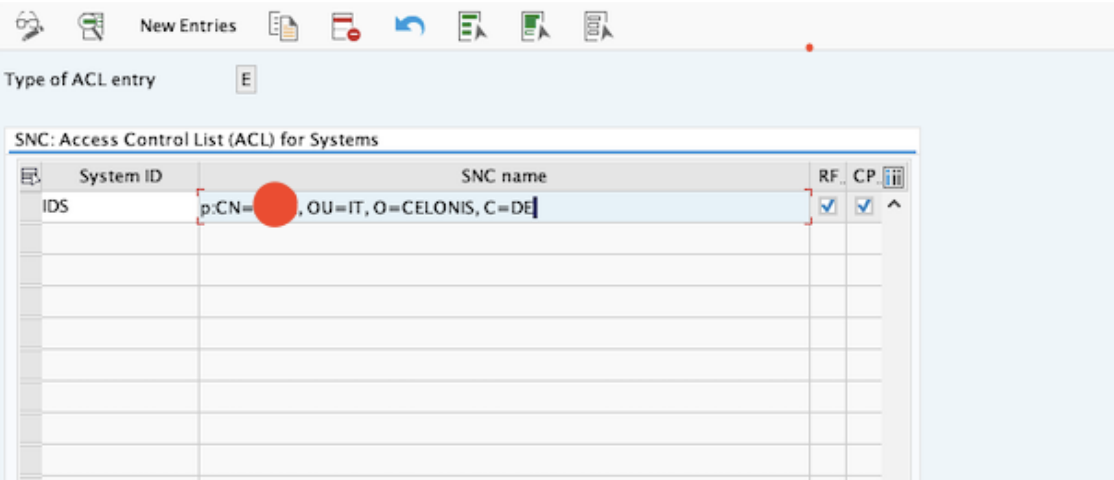
Double-click the entry and enable “Entry for certificate activated”:
Enable Certificate rule mapping:
From the OPC folder, run the following command:
java --add-exports java.base/sun.security.x509=ALL-UNNAMED -jar agent-certificate-generator-<version>.jar x509cert email=<your-email>
Save the generated certificate into a file.
Login into SAP GUI and open t-code CERTRULE.
Upload sample certificate from OPC and click Rule.
Click Display/Change.
Click Import certificate and select the previously generated certificate file
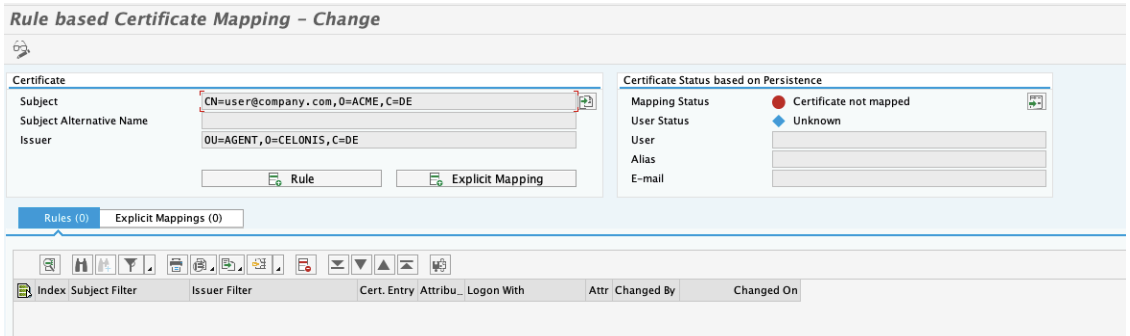
Change Login as to E-Mail and Certificate Attr. to the CN= sample.
The attribute has to be the same as the email address used for the Celonis Platform login.
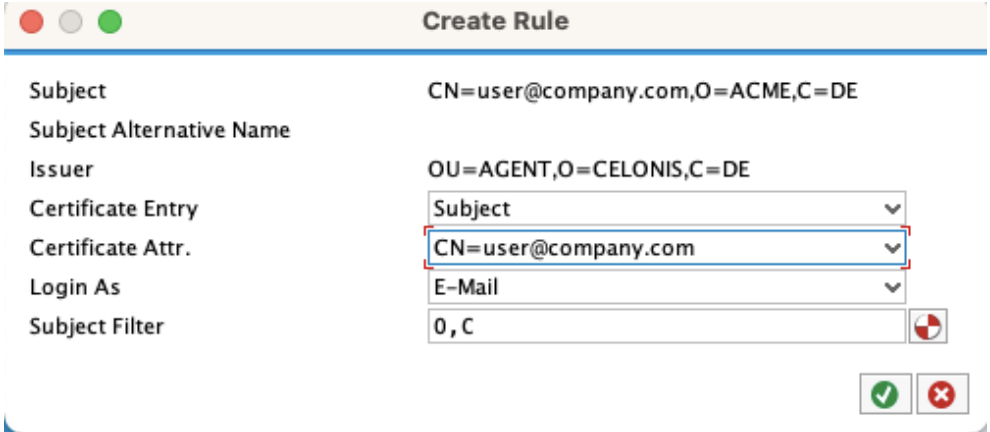
Click Save.
The certificate is now mapped to a user.
In Celonis Platform, go to Studio > Automation (top-right corner) > On-prem system connections.
In the On-prem system connection screen, click Set up on-prem system connections.
In the pop-up, enter a unique system connection name.
Select the on-prem client you want to connect to your application.
From the application list, select SAP.
Specify the configuration details for your application.
For the authentication type, select SSO.
Enter the SNC Partner Name.
This name is the configured SNC name in the SAP server’s security token.
Click Create.
Two keys are generated: systemConnectionID and a JWK. Both need to be copied.
Copy the JSON Web Key (JWK) and systemConnectionId and paste them to the OPC’s application-local.yml file. See the next section for details.
Stop the OPC:
On Windows:
Go to the On-prem Client Management Tool.
In tabs for the automation client and SAP extractor click Stop.
On Linux, MacOS:
Go to the On-prem Client Management Tool. In Terminal run:
./opc-management-tool-cli
In tabs for the automation client and SAP extractor click Stop.
Go to the "Automation agent" folder and open the application-local.yml file.
Add the JWK and systemConnectionId copied in the previous step to the file as shown in the following example:
Note
You can also find these values in the system connection settings under Studio > Automation.
sap-sso: configurations: * jwk: ,\"use\":\"sig\",\"alg\":\"RS256\",\"n\":\"AMQcKjvozCz0yjwzDI0VGGIKLG9UdxGCM8XsAiCxHmql-P9UyTgMzfHDYar1S5JYRrsaR5UX6hIYZ6J9ufRl-qU8UZqNiTFuj0Bolgi3WNCCNrEtFJ1_FC9Jz73q7u_Pkrcml6E2MDzb_XWLMQYRD5SzsH03U0BjtsP8YkLaSDp_kM5mYoy5jAFT9HubOB1DOZtnUyQTGKTJA4OvNxRc5DVQ8zTI6sx1irRpXxe99MRWUYCm4dBr-l7fYVt19x9jZmxcdvfIROe-Mu8Z7DWpIH27zj04sIoAwxoeMxF6-CXjW1C5iTmT-8NbwGalASYz5QYlcAumlNw1e1U-0njrrNk=\"\ ,\"e\":\"AQAB\"}]}" systemConnectionId: abe07d4c-2cc8-416d-8d6d-5d970c56fed5Start the OPC client using On-prem Client Management Tool.
You can now test your system connection. Go to Studio > Automation > On-prem system connections. Next to your system connection, click the settings button and select Test system connection.
See Creating Actions and Creating Tasks.
Note
Optionally, the Analyst can set up the default System Connection when configuring an Action button, eliminating the need for the Business user to specify the (technical) System Connection. If the Analyst does not select a System Connection, the Business user must provide one.
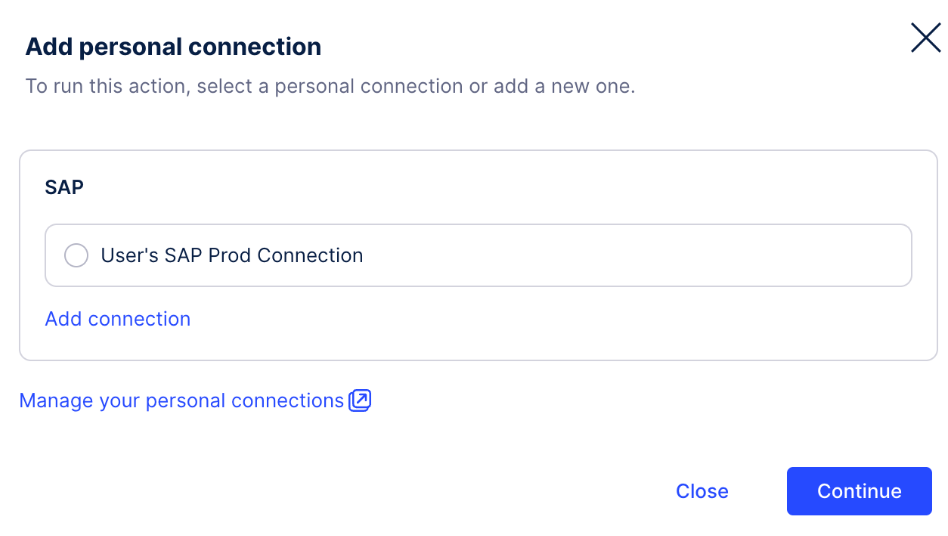
When a user executes the Action Flow by using an Action button, they will be asked to select a personal connection or add a new one.
In order to support the SSO authentication, a solution called “OPC as Secure token service” is being introduced. It provides a seamless SSO integration between the Celonis Platform and SAP systems, where the Celonis on-prem agent/client (OPC) acts as an STS (security token service) that issues short lived X.509 certificates. Please note that the email used to login into the Celonis platform MUST be the same as the user provisioned in SAP.
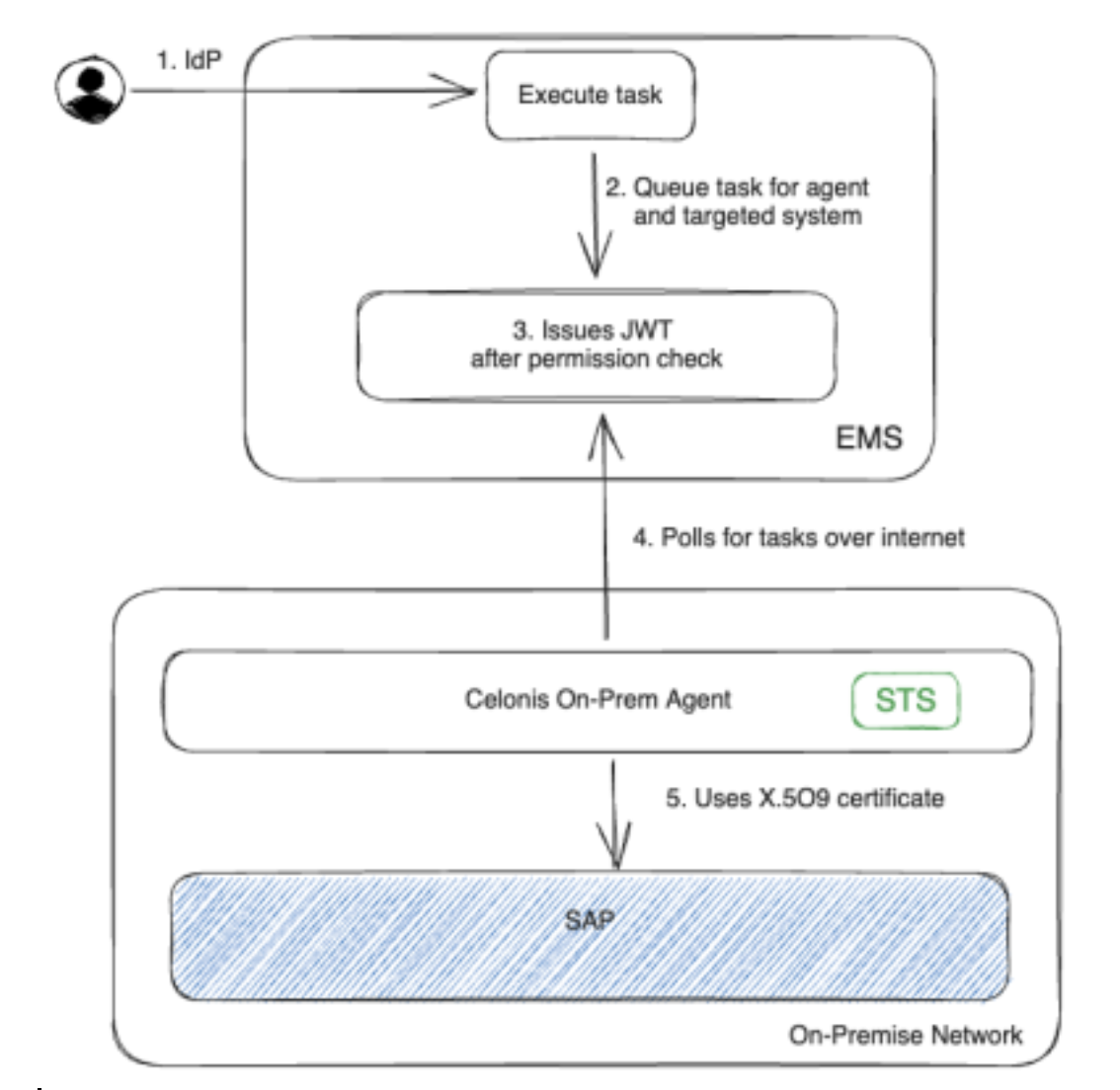 |
User logs in to Celonis Platform via the IdP provider.
User executes a write back task to an SAP source system where SSO is enabled.
The Celonis Platform service verifies the required permissions and issues a JWT token that the agent trusts for the user identity.
OPC polls and receives the signed JWT token from the Celonis Platform that identifies the user based on their email address. It verifies it using a local stored JWKS file (JSON Web Key Set).
OPC issues a short lived X.509 certificate that can be used to log in to SAP and executes the RFC.
Security and privacy
SAP permissions of the user triggering an action in SAP from Celonis are being enforced by SAP, so that no unauthorized action is performed in SAP.
Admin users are able to track in the Celonis Audit log the SAP username (represented by the email address) of the person who performed an action in SAP from Celonis.
It’s also possible to make sure that SAP logs show that an action performed by a specific user was executed from Celonis. Currently available workaround: the source IP is visible in the SAP logs, thus log lines in SAP can be used to identify which actions have been performed via Celonis - via the IP Address (more details available on request).
Technically the Celonis on-prem client connects with SAP using the JCo java library that supports username/password, X.509 and MYSAPSSO2 cookies for authentication.
SAP SSO doesn’t introduce the need to store any personal data (e.g. passwords) in the Celonis platform for SAP SSO (exception: username is stored in the audit logs according to the regulations).
Where is Secure Network Communications (SNC) between the OPC and the SAP server enabled?
The SNC is enabled within SAP.
Which email address do I have to use for the SAP SSO connection?
You must use the same email address you use for logging to Celonis.
When I as a user configures a SSO connection within Celonis, for example in an action, will those connections be shared for other users as well?
Connections are only usable and visible by the user who created them. SAP SSO connections are not shared between users.